Three events occurring in rapid succession on October 7, 2016, stand out in Robby Mook's memory.
The first came at about 3:30 pm. The Obama Administration issued a statement that publicly blamed Russia for hacking the Democratic National Committee and orchestrating the release of the thousands of emails roiling the Democratic Party, which, it said, were "intended to interfere with the US election process." In the day's crazy news cycle, that highly-unusual announcement never had a chance.
At 4 pm, The Washington Post unveiled the infamous Access Hollywood Tape, on which then-candidate Donald Trump was recorded boasting about his own sexual harassment of women. "When you're a star, they let you do it. You can do anything. Grab 'em by the pussy. You can do anything."
Within the hour, yet another media bomb dropped. Wikileaks released another trove of emails—the first 20,000 pages of 50,000 hacked emails stolen from the account of Hillary Clinton's Campaign Chairman John Podesta.

"It was so clear what was happening," recalls Mook, who at the time was a 35-year-old political operative running the Clinton campaign. In time, reporters would dig out old transcripts of paid speeches to Wall Street banks, controversial comments about Catholic voters and other documents that turned out to be damaging to the Clinton campaign. U.S. intelligence has since linked the Podesta trove to the Russian military.
Three years later, as the U.S. gears up for a new presidential election, Mook and other experts expect the Russians to strike again. They'll continue using their modern version of "agitprop" (a mashup of agitation and propaganda) that KGB officers—including a young recruit posing as a translator in Dresden, East Germany named Vladimir Putin—perfected during the Cold War.
The overall intent of the Russians, most intelligence officials and Russia experts agree, has always been to "to spin us up, pit us against each other, sow divisiveness and discord, undermine Americans' faith in democracy," in the words of FBI Director Christopher Wray. Or as Richard Clarke, a former member of the State Department and the National Security Council and a seasoned Cold Warrior, puts it: what the Russians really want is for "the American people to give up on our system."

Many campaigns have already begun practicing better cyber-security hygiene—purging their systems of old emails and text messages every 30 days or so and requiring workers to use two-factor authentication when they log in (verifying their identity from two devices), says Joshua Franklin, a cybersecurity expert who has worked for a wide array of government and private institutions involved in coming up with election security standards, and is consulting for a number of campaigns.
As November 2020 gets closer, a growing army of private citizens, public policy advocates, politicians, state and local election officials and national security agencies are racing to shore up the vast patchwork of security vulnerabilities laid bare by Russia's coordinated campaign of internet mischief during the 2016 election. During the Mueller investigation, Congress gave $380 million to the states to improve their election cyber-security.
Mook has now taken a bipartisan role. In 2017, he partnered with Republican Matt Rhoades, former campaign manager for Mitt Romney's 2012 presidential campaign, to establish the Defending Digital Democracy Project (D3P), at a Harvard University-affiliated think tank. The aim of the organization is to protect democracies from cyber and information attacks. Last month, a D3P spinoff won approval from the Federal Election Committee, to provide free and low-cost cybersecurity services to political campaigns without violating campaign finance laws.
Now that Mook and his collaborators have won that approval, more campaigns will be able to deploy cutting age pattern recognition software of the type used by banks to spot fraudulent activity to monitor for likely spear-phishing emails and the unusual export of large datafiles, says Crane Hassold, a former FBI cyber expert and senior director of threat research at the cybersecurity firm Agari.
The precautions the campaigns are taking now tend to address yesterday's problems, such as the DNC hack that was ultimately so damaging to the Clinton campaign in 2016. The worry of intelligence and security experts is what the Russians are likely to do in 2020 that somehow was either overlooked in the aftermath of the last two elections or comes out of the blue. "We recognize that our adversaries are going to keep adapting and upping their game," the FBI's Wray said to the Council on Foreign Relations in April.
To understand how Russia plans to undermine Americans' faith in the U.S. democratic system, cyber-security experts and campaign officials are digging through the aftermath of the elections of 2016 and 2018 for clues. There's a lot to worry about.
The Propaganda War
Shortly before the 2016 election, University of Washington researcher Kate Starbird began studying the online conversations of the #BlackLivesMatter movement. She and her team followed some of the most active Twitter accounts and tracked the influence of their tweets.
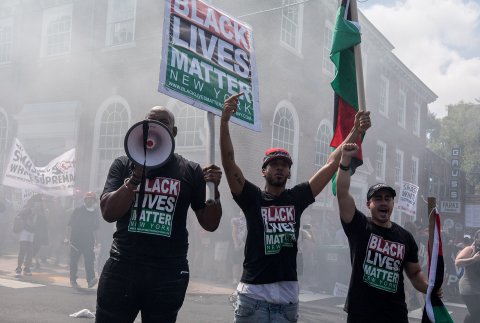
Starbird, who studies human-computer interaction, was primarily struck by how toxic much of the content was—and how vitriolic and polarized the debate had become, with some advocating violence and others using racist language. Then, just a few weeks after the team published its first paper on the topic in October 2017, representatives of Facebook admitted to congressional investigators that they had traced ad sales totaling more than $100,000 to a shadowy Russian company known as Russia's Internet Research Agency (IRA), with a history of pushing pro-Kremlin propaganda. The US Intelligence community had already concluded that Russia paid social media trolls to spread fake news and influence public opinion. The ads had focused on politically divisive issues such as gun rights, immigration, and racial discrimination.
The news got Starbird and her team wondering if any of the trolls engaged in any of the conversations she had studied. In November, when the House Intelligence Committee released a list of accounts given them by Twitter associated with IRA, Starbird and her team decided to take a look and see if they recognized anyone. They were stunned by what they discovered. Dozens of the accounts in the list appeared in their data—some among the most retweeted. IRA accounts were also masquerading as genuine #BlackLivesMatter and #BlueLivesMatter activists.
When Starbird and her team went back into their data from 2016, they found that IRA internet trolls had set up parallel operations that worked in close concert, allowing them to play both sides of the fence. They adopted the personas of online activists, infiltrating communities, and mimicking the sentiments of other participants, and then, when the opportunity struck, acting as influencers, subtly and not so subtly shaping the conversations. Some adopted relatively mild personas, sticking with the pack, building a trusted brand. Others were bomb throwers, adopting caricatures of US political identities and fanning the flames of dissent. "They targeted both Black Lives Matter conversations on the left, and then online conservative activism on the right," she says.
"So on the left and in the pro Black Lives Matter group, you could have accounts like 'bleep the police' who are calling police pigs and advocating for violence against police, and some of the IRA trolls are saying some of the worst things in that kind of vein," Starbird says. "And then on the right they are using racial epithets and saying some of the nastier things. In some cases, you have their troll on one side arguing with their troll on the other side just to say nasty things to each other."

In 2016, Russian online personas would put in a good word for Trump on the right and denigrate and try to get people not to vote for Hillary on the left. In 2020, Starbird expects these same trolls to ramp up their efforts to "divide the left." With a crowded field of candidates vying for attention, trolls may adopt personas aligned with specific candidates, infiltrate discussions and then, whenever possible, use their positions to attack other Democratic candidates (likely supported by other personas created by the trolls in the cubicles next to them) and depress the eventual vote.
"You'll see them mimicking regularly the "resist" and other sorts of Democratic personas, and start denigrating the other candidates," she says. "And especially once the Democrats choose a candidate, they'll denigrate the chosen candidate, and say, 'Oh this person doesn't represent us. We can't vote for them. Therefore, I'm not going to vote'."
Countering the Trolls
This time, the trolls no longer have the advantage of surprise. Efforts are underway to block them or reduce their influence.
Under mounting political pressure, both Facebook and Twitter have vowed to shut down the trolls. Before the 2018 mid-term election, the FBI identified dozens of accounts and pages operated by the IRA. Facebook promptly inactivated them. It also set up a "war room" to monitor threats as they emerged in real time.

Federal agencies, meanwhile, have ramped up efforts to help voters spot bots and disinformation campaigns. Election officials in West Virginia, Iowa, Kansas, Ohio and Connecticut plan to include disinformation education in their voter education programs.
The military's Cyber Command has also been active. Before the 2018 election, they launched a campaign to deter the Russians behind the 2016 influence campaign, warning Russian operatives to cease their efforts and knocking a troll farm run by the IRA offline for several days.
But no one is under any illusions about the challenges that lie ahead. We expect Russia to continue "to focus on aggravating social and racial tensions, undermining trust in authorities, and criticizing perceived anti-Russia politicians," Director of National Intelligence Dan Coats told the Senate Intelligence Committee in January. "Moscow may employ additional influence toolkits—such as spreading disinformation, conducting hack-and-leak operations, or manipulating data—in a more targeted fashion to influence US policy, actions, and elections."
Not only did the Russians continue their tactics through 2018, says the FBI's Wray, "but we've seen an indication that they're continuing to adapt their model, and that other countries are taking a very interested eye in that approach".
The rhetorical goal remains the same as it has always been. "They want the American people to think that politics and politicians are awful," Clarke says. "That there's gridlock, nothing gets done. They want us to be inward-looking, at each other's throats."
The desire to promote cynicism and division also helps to explain another key part of the Russia's 2016 attacks—and why we should be so worried about our 2020 vulnerabilities: Russian efforts to penetrate our election infrastructure.
Hack the Vote
Susan Greenhalgh can't say for sure the Russians successfully hacked into the voter registration system of Durham County, in the swing state of North Carolina back on election day 2016 and caused the widespread chaos she witnessed unfold. Nor can she offer up any proof they were behind the curious problems with voter registration rolls that gummed up the works in Ohio, Pennsylvania, Indiana, Georgia and Florida on election day 2018.
But if somebody wanted to strategically depress vote counts, piss off lots of people, and cast the veracity of U.S. elections into question on the local level, it seems to Greenhalgh it would probably look a lot like what she watched unfold in real time on both those election days. None of those incidents have yet been fully investigated—some of them not at all. In Florida, according to the Mueller report, a voting system in at least one county was hacked in 2016 (the governor and county officials are keeping mum about which one).
Greenhalgh worries what might be in store for November 2020.
Greenhalgh, a former chemical commodities broker, abandoned finance in the early 2000s and found her new calling advocating for election security. As counties around the nation began moving to electronic voting and electronic voter registration systems, she began working for organizations calling for paper ballots and other protections against malfunctions, hacking and fraud. She also began volunteering for rapid response election monitoring groups on hand to solve any issues on election day that might interfere with the constitutionally protected right to vote. In 2016, she manned a vast call center in a law office in midtown Manhattan on the morning of election day. She had been assigned to a group tasked with monitoring and responding to problems in North Carolina – and the calls began almost as soon as the polls opened at 6:30 am.
The electronic version of the voter registration rolls, loaded onto the laptops and tablets that poll workers used to check in voters, appeared to be incorrect – as scores of voters were told they had already voted, when they insisted they had not. Other poll workers found themselves unable to look up any digital information at all.

The problems were so widespread that within just a few hours county election officials had decided to abandon the electronic version of the registration rolls altogether and do things the old-fashioned way. Which created a new series of problems: as poll workers scrambled for paper versions of the voting rolls and paper forms required by law, long lines formed and tempers boiled. Voting was halted for two hours in one precinct. In the meantime, scores of voters gave up and went back to work or went home, thoroughly discouraged.
"It took hours for the line to work through and dissipate," Greenhalgh says. "So it really did have an impact on people's ability to vote that day."
To Greenhalgh it seemed suspicious. A couple weeks earlier, CNN had reported that a voting system vendor had been attacked by Russian intelligence and the FBI was investigating. She'd heard through her contacts that the name of the vendor was VR Systems. Then around midday, buried in a news story, she read a sentence that stopped her cold: Charlotte had signed a contract just a year before with VR Systems to use their electronic poll book systems. Greenhalgh reached out to the Department of Homeland Security.
"They were very interested," she recalls.
Nevertheless, it wasn't until this June that the DHS revealed in an interview with The Washington Post they finally planned to conduct a forensic analysis of the laptops used during the election—a request North Carolina elections officials did not make until months after the election, insisting they could carry out an investigation on their own. In the interim, Mueller and his team filed indictments detailing the activities of Russian intelligence operatives, and then issued his long-awaited report. They confirmed that in the weeks before the 2016 elections, Russian intelligence agents not only attempted to hack VR Systems, they also sent "spear-phishing" emails to 122 local elections officials who were the firm's customers (personalized emails, in other words, designed to trick them into clicking on links or opening attachments that would allow hackers to penetrate accounts). And that the same Russian military unit had probed at least 21 state systems, looking for vulnerabilities.
The Mueller Report itself noted that in August 2016 Russian military intelligence had managed "to install malware on the company network" of one unnamed voter registration technology vendor in the United States. That company is widely suspected to be VR Systems, Greenhalgh says.
VR Systems has acknowledged that Russian hackers, in an apparent attempt to penetrate its voting systems, sent email phishing attacks to employees and customers. It insists that none of its employees' email accounts were compromised and that it promptly warned all its customers of the attack. "No one indicated to us that they had opened the email," the company said in a statement. The company says it has cooperated all along with law enforcement and has tightened its cyber-security.
In the meantime, Greenhalgh's concern over the vulnerabilities of the election infrastructure have only grown. In fact, during the 2018 mid-term elections, she watched the same thing happen. This time, problems were reported in other states, too. In Ohio, Pennsylvania, Indiana and Florida, some voters showed up and were told, incorrectly, that they had already voted on absentee ballots. In Georgia, some voters showed up at the polling stations where they had been voting for years to find their addresses had been changed and no longer matched those on their IDs. Others learned that their registrations had suddenly disappeared.
In most of these cases, Greenhalgh says, technology was once again involved.
She's not ready to give either the 2016 or 2018 elections a clean bill of health. She is not persuaded by DNI's Coats, who told Congress in January that the US "does not have any intelligence reporting to indicate any compromise of our nation's election infrastructure that would have prevented voting, changed vote counts, or disrupted the ability to tally votes" in either 2016 or 2018.
Whether her suspicions are warranted or not, it probably doesn't matter much to the Russians. Their primary goal isn't to change the outcome—it's to undermine confidence. In other words: It doesn't matter if the vote was rigged. The operation is successful if U.S. citizens just think it was rigged.
So, What Can Be Done?
Sure, efforts are underway to shore up protection of the election infrastructure. The trouble is this: the U.S. elections system is spread out and administered by thousands of individual county, city and town election officials – many of whom jealously guard their autonomy from the federal government. Electronic voting machine manufacturers have cultivated cozy, revolving door relationships with local and state election officials.
This helps explain what to some election security advocates seems inexplicable: Legislation that would set new cybersecurity standards for all federal elections has been stalled in the U.S. Senate for months. (Senate Majority Leader Mitch McConnell has so far refused to bring it up for a vote).
"Part of the Mueller Report was just a cri de coeur about how we need to be more prepared and we haven't done enough in the face of a clear attack on our elections," Lawrence D. Norden, Director of the Election Reform Program at the Brennan Center for Justice at New York University School of Law says. "And it is amazing how little has been done to patch up some of these vulnerabilities."
Many of these systems, he notes, have gaping security holes. Electronic poll books of the type that caused so many problems in Durham back in 2016 are used in at least 34 states, Norden says. Often the information is on the cloud, or maintained with wireless components for which no federal security standards have been established. As of May 2017, at least 41 states were using voting systems that are more than a decade old, running software no longer serviced or provided security patches.
At least 11 states, meanwhile, continue to use paperless voting machines in at least some counties and towns - despite warnings from the National Academy of Science, the Senate and House Intelligence Committees and the DHS that they need to replace them with a system that at the very least has paper backups.
The private vendors in charge of producing and programming voting machines and maintaining registration databases—and even in some cases tallying election night returns—are not regulated. "We don't know basic things like who they employ, what kind of screening process they have around security, what their cybersecurity best practices are, who owns them, even who they are, how many there are," Norden says.
What We Don't Know
To many the most alarming thing about the Russians and 2020 is that we don't know what's coming.

"What I'm worried about is that we're only thinking about preventing a repeat of 2016," says Rob Knake, a former director of cybersecurity policy at the National Security Council, and the coauthor of a new book with Richard Clarke on cyber security.
He adds: "It's the nature of cyber conflict that when you close off one avenue, the attackers don't give up and go home ... the Russians will be looking at alternative ways to influence the election, or directly interfere in voting this time."
Intelligence officials have already identified one relatively new weapon. In his testimony before Congress, Coats warned that the Russians might try to sow chaos with "deep fakes"—doctored videos that depict things that never happened. Software is now widely available that makes it easy to paste a person's face on another person's body. A chilling foreshadowing came in May when a low-tech doctored video of House Speaker Nancy Pelosi slurring picked up millions of views on Facebook.
"The most severe escalation might be the introduction of a deep fake—a video of one of the candidates saying something they never said," House Intelligence Chairman Adam Schiff said last spring. "If you look back at how impactful the Mitt Romney videotape about the 47 percent was, you could imagine how a videotape that is more incendiary could be election-altering. This may be the future we are heading into."
Clarke's biggest concern is that the Russians will penetrate voter rolls in key swing states and create chaos aimed at strategically depressing the vote enough to raise more questions about the legitimacy of the election outcome.
In the end, the most powerful tool we have to combat the efforts has little to do with technology. While die-hard Clinton loyalists continue to maintain that the scale of the 2016 hacks constituted an unprecedented attack on our democracy, many seasoned Cold Warriors prefer to place it in a larger context. By historical standards, some argue, our bellicose Slavic foes have employed far more aggressive tactics.There was a time, after all, when they controlled unions and could mobilize thousands to agitate on their behalf.
"None of this works because they're good," says Edward Lucas, a British writer and security policy expert, whose many books include The New Cold War: Putin's Russia and the Threat to the West. "It all works because we're weak."













